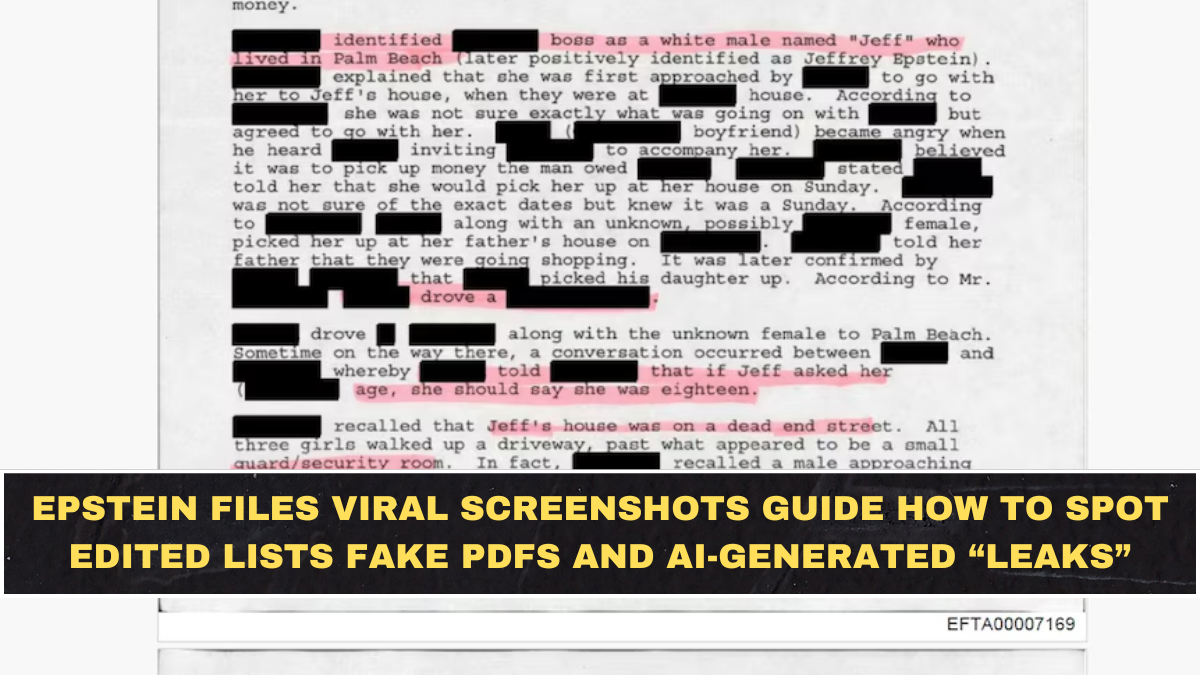
Whenever Epstein-related topics trend, the internet fills with so-called “leaks” claiming to reveal hidden truths. These posts often arrive as screenshots, PDFs, or neatly formatted lists that look official at first glance. The speed at which they spread makes them feel urgent and credible, even when they are not.
This article breaks down how these fake leaks are created, why they work so effectively, and the specific warning signs readers can use to spot manipulated material before sharing it further. The goal is not to dismiss real reporting, but to protect readers from being misled by content designed to exploit outrage and curiosity.

Why Fake Epstein Leaks Appear During Every Spike
High-interest topics create opportunity. When attention surges, bad actors know people are less likely to slow down and verify what they are seeing. Epstein-related content is particularly vulnerable because many people already expect secrecy and cover-ups, which lowers skepticism.
This environment rewards speed and shock value. Fake documents thrive because they match what people emotionally expect to find, not because they are grounded in reality.
The Most Common Types of Fake “Leaks”
Most viral Epstein leaks fall into a few predictable categories. These include typed name lists presented as “unsealed files,” PDFs that mimic legal formatting, and screenshots claiming to show internal emails or memos. Some even combine real excerpts with fabricated additions to feel authentic.
The danger lies in mixing truth with fiction. A single real paragraph surrounded by fake material can make the entire document feel legitimate.
Red Flag 1: No Clear Document Origin
Legitimate legal documents always have an identifiable origin. Fake leaks rarely explain who created the document, under what authority, or for which legal purpose. Vague phrases like “just released” or “finally exposed” are common substitutes for real sourcing.
If a document cannot clearly explain where it came from, skepticism is warranted.
Red Flag 2: Inconsistent Formatting
Real court filings follow strict formatting standards. Fake PDFs often show inconsistent fonts, irregular spacing, missing page numbers, or mismatched headers. These may seem minor, but they are strong indicators of manual editing.
Careful inspection usually reveals these inconsistencies quickly.
Red Flag 3: Names Presented Without Context
One of the most powerful manipulation tactics is listing names without explanation. Legitimate documents explain why a name appears, whether as a witness, contact, or logistical reference. Fake lists strip all context to provoke assumption.
Context removal turns information into accusation, which is precisely the point.
Red Flag 4: Emotional Language in “Official” Documents
Legal records are dry by design. Fake leaks often include dramatic phrasing, moral judgments, or sensational headings that would never appear in real filings. This emotional tone is meant to guide interpretation rather than inform.
When a document feels written for outrage, it likely is.
Red Flag 5: Screenshots With No Metadata
Screenshots are easy to manipulate and difficult to verify. Fake Epstein leaks often rely on cropped images with no timestamps, no visible source, and no surrounding context. AI-generated screenshots now make this even easier.
Absence of metadata is not proof of authenticity; it is a warning sign.
Red Flag 6: Claims of “Too Dangerous to Share”
Posts that claim information is being suppressed often encourage urgency. Phrases suggesting censorship or imminent deletion are designed to bypass critical thinking and push rapid sharing.
Legitimate reporting does not rely on fear-based sharing tactics.
Red Flag 7: AI-Generated Text and Layout
Recent fake leaks increasingly use AI to generate professional-looking text. While grammatically clean, these documents often lack legal precision, misuse terminology, or blend unrelated concepts in ways experts would not.
Polish should never be mistaken for accuracy.
Red Flag 8: Recycling Old Material as “New”
Many viral leaks are simply old documents repackaged. Dates are removed, filenames changed, and excerpts reshuffled to appear fresh. Without timestamps, readers assume novelty where none exists.
Always question whether the content is actually new or just newly framed.
Red Flag 9: No Corroboration Anywhere Else
Real disclosures create ripple effects across multiple credible outlets and institutions. Fake leaks exist in isolation, circulating only through social media and messaging apps.
If no independent confirmation exists, caution is necessary.
Red Flag 10: Overly Clean “Lists”
Reality is messy. Fake leaks favor tidy lists with clear villains and no ambiguity. This neatness is appealing but unrealistic in complex legal cases.
Simplicity is often a sign of fabrication.
Red Flag 11: Calls to “Do Your Own Research” Without Tools
Encouraging readers to “research” without providing verifiable paths is another manipulation tactic. It shifts responsibility away from the claim-maker while reinforcing belief.
Research requires sources, not slogans.
Red Flag 12: Pressure to Share Immediately
Urgency is the final and most powerful tool. Fake leaks thrive when people feel they must act now. Slowing down is often enough to expose inconsistencies.
Time is the enemy of misinformation.
Conclusion: Skepticism Is a Public Service
Fake Epstein leaks succeed because they exploit emotion, not evidence. Learning to recognize red flags protects not just individual readers, but the broader information ecosystem. Accuracy matters most when topics are sensitive and stakes are high.
Choosing not to share unverified material is not silence; it is responsibility.
FAQs
Are all Epstein-related leaks fake?
No. Some documents are real, but many viral “leaks” are manipulated or fabricated.
Why do fake PDFs look so convincing?
Modern tools and AI make professional-looking forgeries easy to create.
Is a screenshot ever reliable evidence?
Rarely on its own. Screenshots require context and verification.
Why are names often listed without explanation?
To provoke assumption and emotional reaction.
How can I verify a document quickly?
Check origin, formatting, context, and whether it’s confirmed elsewhere.
What’s the safest action if unsure?
Do not share until authenticity is clearly established.